In today’s digital age, where information and technology dominate nearly every aspect of our lives, online privacy and security have become more critical than ever. As more of our personal and professional activities transition to the online world, the demand for secure communication methods continues to grow. Understanding how online communication works and the technologies available to protect it is essential for navigating this landscape safely. One prominent solution for enhancing online privacy and security is the use of Virtual Private Networks (VPNs). VPNs have emerged as a powerful tool for ensuring secure communication, protecting sensitive data, and maintaining anonymity in an increasingly interconnected world.
Definition of VPN
VPN stands for Virtual Private Network.
Virtual in VPN refers to the creation of a software-based pathway that substitutes the direct physical layer of network communication (including routers, switches, and other hardware). While the data still travels over these physical devices, the VPN software reroutes it through an encrypted tunnel, making it appear as though the connection is private and direct.
Private in VPN refers to the connection being secure and encrypted. This ensures that internet service providers, hackers, or anyone who might intercept network traffic cannot view the content of the data or determine its origin.
Network in VPN refers to a group of devices that communicate with each other. In the context of using a VPN, this typically involves personal devices (such as computers, mobile phones, or tablets) connecting to VPN servers to securely exchange data.
Together, these elements create a secure tunnel over traditional network communication protocols, providing users with privacy, security, and anonymity online
How does network communication work
Before explaining how virtual private networking works, it is important to first understand the basics of network communication. Network communication is structured in layers, each governed by specific protocols. These layers are defined in the OSI model, which consists of seven layers. However, to understand VPN functionality, a deep understanding of every layer is unnecessary and brief summary will suffice.
OSI model:
Application layer:
This layer interacts directly with the user and is responsible for enabling communication between applications and the network. For example, when a user wants to read an email or load a web page, the corresponding application (such as an email client or web browser) uses application layer protocols to initiate communication. The most common protocols in this layer are HTTP or HTTPS (the secure version of HTTP) for web browsing, and SMTP (Simple Mail Transfer Protocol) for emails.
Presentation layer:
The presentation layer is responsible for preparing and formatting data for other layers. This includes tasks such as data compression and handling encryption when required. Additionally, if the application requesting the data uses a different encoding format, this layer converts the data to ensure it is interpreted correctly by the application.
Session layer:
The session layer is responsible for establishing, maintaining, and terminating connections between devices, enabling them to transfer data. These connections are referred to as sessions. To ensure efficiency, the session layer sets checkpoints that track how much data has already been transferred. If the connection is interrupted, the transfer can resume from the last checkpoint instead of starting over from the beginning.
Transport layer:
The transport layer is responsible for managing the transportation of data between devices. It divides the data into smaller pieces called segments, which are then sent individually. This layer also manages the flow and speed of data transfer, ensuring compatibility in cases where one device has a slower internet connection.
There are two main protocols used at the transport layer: TCP and UDP. TCP (Transmission Control Protocol)ensures reliable delivery of all segments, making it suitable for transferring web page source code, documents, and other data where accuracy is critical. It
performs error control to verify that all data has been successfully transported. UDP (User Datagram Protocol), on the other hand, is used when some data loss is acceptable, such as in streaming or online meetings, as it prioritizes speed over reliability.
Network layer:
The network layer is responsible for breaking down segments from the transport layer into smaller pieces called packets. If the devices are on the same network, this layer may not be necessary. However, when devices are on different networks, IP addresses become essential. The network layer assigns each packet a source IP address (identifying the origin device) and a destination IP address. It then determines the most efficient path for the packet to reach its destination.
Data link layer:
The data link layer is similar to the network layer but operates within the same local network. It manages data transfer between devices on the same network and breaks packets into smaller pieces called frames. Unlike the network layer, which uses IP addresses, the data link layer uses MAC addresses to ensure data is delivered to the correct device within the local network.
Physical layer:
The physical layer is responsible for transmitting the actual data as a stream of 0s and 1s over physical mediums such as cables and switches.
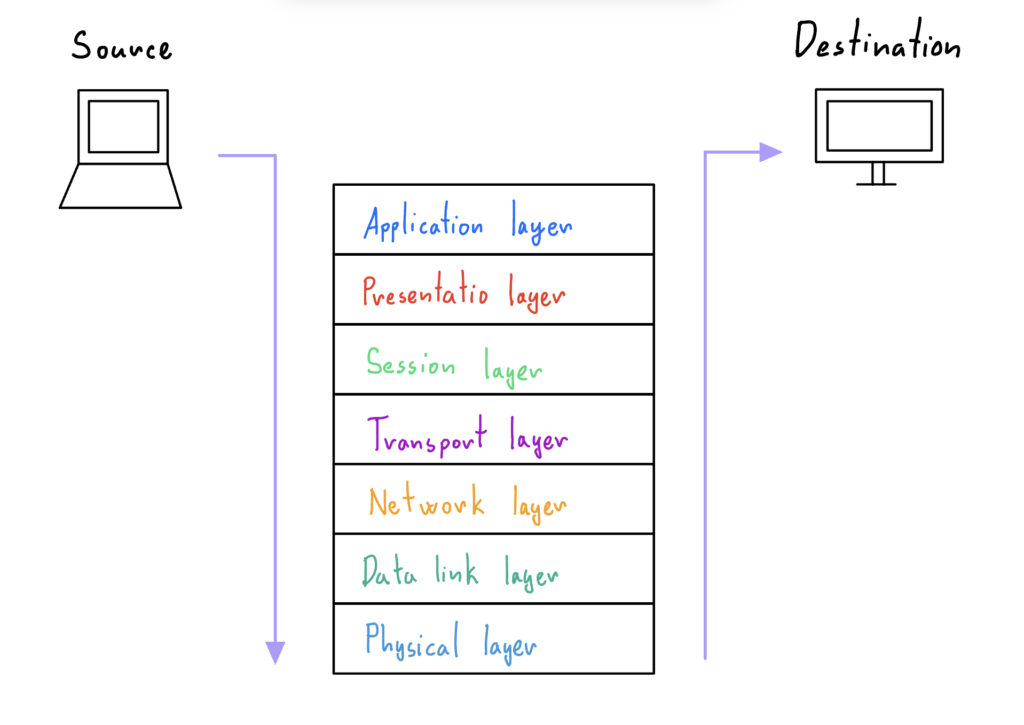
The layers of the OSI model work together to facilitate communication. On the source device, data flows from the top layer (application layer) down to the bottom layer (physical layer) in a process called encapsulation, where each layer performs its specific function on the data. After the data is transmitted to the destination device, it moves through the layers in reverse order from the physical layer up to the application layer—ensuring the data is properly interpreted.
How does VPN work
Virtual Private Networks (VPNs) operate on top of the OSI model and are designed to provide security and anonymity. A VPN creates a secure tunnel between your device and the VPN server, encrypting all communication to ensure it remains private. Once the data reaches the VPN server, it is encapsulated into a new packet with the server’s IP address. This process ensures that the destination you are connecting to (such as a website, school server, or streaming platform) only sees the VPN server’s IP address, not your own.
Types of VPN
There are two most common types of virtual private networks: Site-to-site and Remote access VPN.
Site-to-site:
Site-to-site VPNs are commonly used in corporate environments where companies have multiple branches within their infrastructure. The primary purpose of a VPN in this scenario is to enable the secure sharing of company resources, such as documents, files, applications, and databases, across different locations.
For example, a company may have its headquarters in one city, such as Prague, where the local network includes storage servers for company files and projects, as well as databases containing sensitive company data. If the company has a branch in another city, such as Brno, the branch would need secure access to these resources. This is achieved through a site-to-site VPN, which establishes a secure and encrypted connection between the two locations, allowing seamless communication and resource sharing.
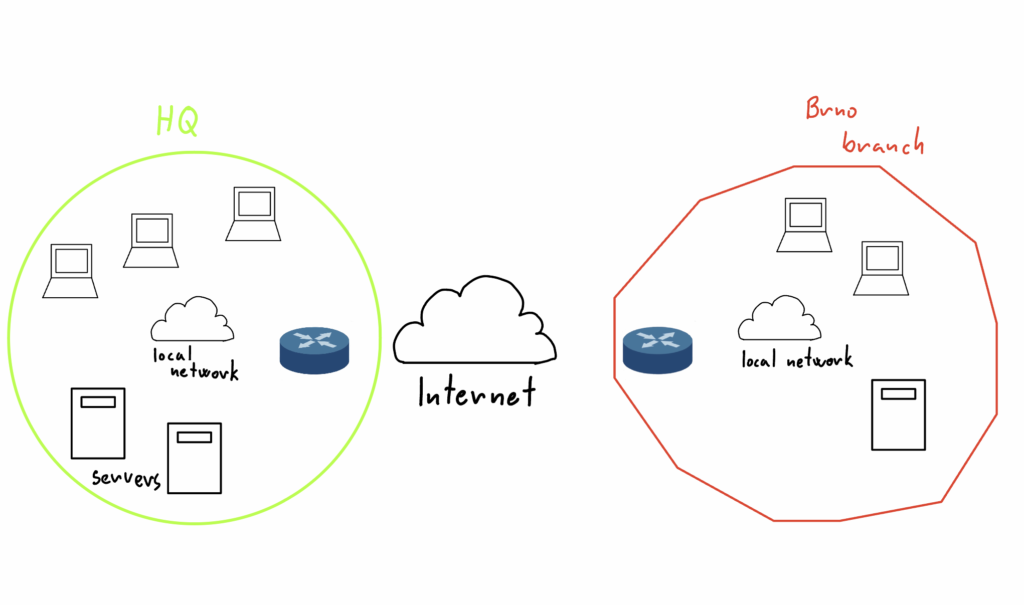
Site to site VPNs requires VPN routers or VPN gateways. A VPN gateway is a device or software that establishes a secure connection between the sender and receiver networks. It receives data from the source device on the local network, encrypts and secures the data, and encapsulates it into a new packet with a new IP header of the gateway.
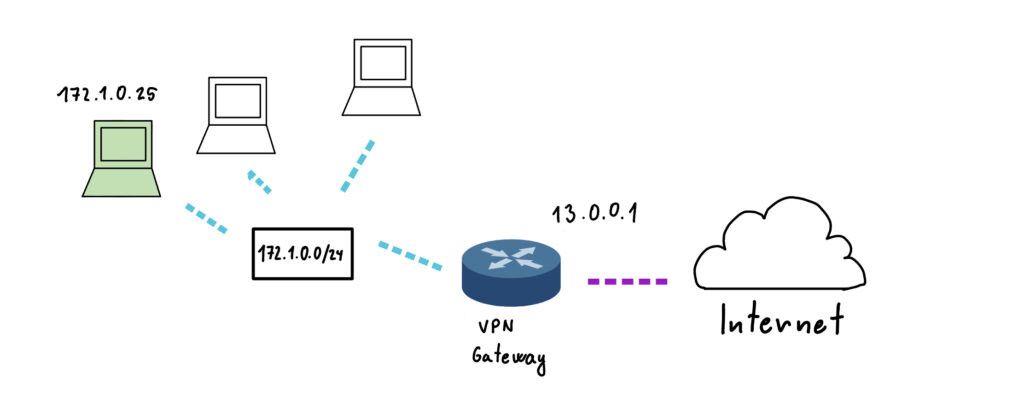
Let’s explore more about VPNs by examining the network interfaces after connecting to a VPN through a client application. I am using macOS, but the principles I will discuss are universal and not limited to a single operating system.
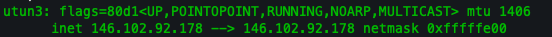
The utun3 interface seen above is a virtual tunnel interface that serves as the endpoint for our VPN connection. Unlike physical network interfaces, such as Wi-Fi or Ethernet cards used by our computers, this interface exists only in software and is managed by the VPN client application. It is responsible for encrypting our traffic and passing it to the physical network card, which then transmits the encrypted data over the internet to the VPN server (in this case, our school’s VPN server). TUN stands for network TUNnel and is used by many VPN systems such as OpenVPN, ZeroTier, WireGuard.
VPN protocols
VPN protocols, sometimes called tunneling protocols, are the rules and technologies that handle everything we have described so far about VPN functionality. They define how data is encrypted and securely transmitted between devices while ensuring the connection remains stable and efficient. Several protocols are commonly used, including:
- OpenVPN
- WireGuard
- IKEv2/IPsec
Each of these protocols, along with others, offers unique functionality and is designed for specific tasks. They differ in key aspects such as data transfer speed, encryption algorithms, and operating system support.
Paid VPN services
In recent years, paid VPN services have gained significant popularity, largely due to sponsorships with influencers and YouTubers who promote these services in their posts and videos. To use them you need to pay subscription (monthly, yearly) and download their client. These services fall into the category of remote access VPN. There are many to choose from. According to Security.org, NordVPN is rated as the best VPN service for 2024, followed by Surfshark in second place and Private Internet Access VPN in third place (Security.org, 2024).
The most common claims made by these services include enhanced security on public networks (such as in coffee shops), where using a VPN prevents others from intercepting your data. Additionally, they often advertise the ability to unlock content from other regions, bypassing restrictions on access to certain websites or streaming platforms.
While VPN services claim to secure all data on public networks, this is an overstatement in most cases. Modern websites already use HTTPS, which provides encryption through TLS (Transport Layer Security) protocols. This ensures that user data remains private and secure from eavesdropping, even on public Wi-Fi networks.
Here we can see that the VŠE university website uses SHA-256 encryption, which is the same encryption algorithm utilized by the OpenVPN protocol for secure communication (OpenVPN, n.d.).
Paid vs open source
When deciding between a paid VPN service and an open-source VPN solution, it is essential to consider your specific needs and intended use. For business purposes, open-source VPN solutions are often the better choice as they offer significantly more control and customization. Businesses can configure these solutions to meet their unique security and performance requirements, though this typically requires technical expertise.
For the average user, the decision is more nuanced and depends largely on the purpose of the VPN. If the primary goal is securing data while browsing the internet, a VPN may not always be necessary, as discussed earlier, due to modern websites and applications using secure communication protocols such as HTTPS. However, if the purpose is to bypass geo- restrictions (e.g., accessing region-locked content), paid VPN services are generally the better option. Paid services provide access to a vast network of servers in multiple locations at a lower cost than setting up and maintaining private VPN servers.
Additionally, paid VPN services often offer better convenience and reliability. These services are managed by dedicated organizations with the resources to monitor and maintain the network, ensuring high availability and security. In contrast, open-source VPN solutions, while powerful, may introduce a higher risk of misconfiguration or technical issues, especially if managed by less experienced users. For critical communications, the robust support and oversight provided by paid VPN providers reduce the risk of failure.
Conclusions
Virtual Private Networks are a powerful tool for enhancing online security and privacy, offering solutions for both individuals and organizations. They provide a secure and encrypted way to communicate over the internet, protecting sensitive data and enabling access to restricted content. As explored in this essay, VPNs come in various types, such as site-to-site and remote access VPNs, each serving different purposes. Furthermore, the choice between paid VPN services and open-source solutions depends on individual needs, technical expertise, and specific use cases. Paid VPNs offer convenience, broad server networks, and professional support, while open-source solutions provide flexibility and control for those who require custom configurations.
Ultimately, understanding how VPNs work, the protocols they use, and their strengths and limitations is essential for making informed decisions about securing our online activities in an increasingly digital world. By choosing the right VPN solution, we can enhance our privacy and ensure safe communication in our interconnected lives.
List of references
Security.org. (2024). The best VPNs of 2024. Retrieved December 6, 2024, from https://www.security.org/vpn/best/
OpenVPN. (n.d.). What is OpenVPN?. Retrieved December 6, 2024, from https://openvpn.net/faq/what-is-openvpn/
Baeldung. (2021, August 18). The purpose of the TUN interface in Linux. Baeldung. Retrieved December 6, 2024, from https://www.baeldung.com/linux/tun-interface- purpose
Surfshark. (2021, September 8). VPN protocols: What are they and how do they work? Surfshark. Retrieved December 4, 2024, from https://surfshark.com/blog/vpn- protocols
Vaňout Ondřej. (2024). VPN interface. Terminal output from personal computer.
Vaňout Ondřej. (2024). HTTPS certificate. Screenshot of webpage certificate from personal computer.