Introduction
Computer viruses have come a long way since they first appeared in the 20th century. Evolving from simple programs that started as experiments, to becoming powerful tools for stealing data, destroying important documents, extortion and even found their use in political and military circles. Today, computer viruses play a major role in our everyday life on the internet. But how did we get here? This paper focuses on the biggest, most destructive computer viruses in history starting from the first computer virus created and moving through time up until modern day, with an outlook on the future of computer viruses.
Types of computer viruses
While computer virus is probably the most used term to describe harmful programs, its usually not used properly. A better term for that would be malware, with computer virus being a type of malware.
Malware
Malware is an abbreviation for malicious software. It is a broad term for every computer program, which is intentionally written to cause harmful action. For example, stealing data, deleting information, gaining unauthorized access, corrupting files and many other.
Computer virus
A virus is a type of malware whose main characteristic is the ability to self-replicate by infecting other computer programs. It spreads by inserting itself into the code of other programs or files. When the infected program is executed, the virus is also triggered, allowing it to multiply. Viruses typically require human action (such as opening a file or running a program) to spread. By injecting themselves into other programs, computer viruses can make these programs not function properly, slow down the system, corrupt data and other harmful actions.
Worm
Worm is a type of malware similar to a computer virus but with one key difference: it’s usually a standalone program, meaning it can replicate without infecting other programs and doesn’t usually require human interaction. Worms try to find vulnerabilities in a system to replicate and spread to other computers. This usually slows down the system by overwhelming the network usage. Since worms do not rely on infecting other programs to spread, they can be harder to detect.
Trojan horse
Trojan horses disguise themselves as legitimate programs to trick users into installing them. They cannot spread by themselves, instead relying on users to install or share them. Trojan horse programs usually deliver other malware such as backdoors or spyware.
Ransomware
Ransomware is a type of malware that encrypts a victim’s files or locks them out of their system. The attacker demands a ransom (usually in cryptocurrency) to provide the decryption key or restore access to the system. These attacks usually target corporations or wealthy individuals with sensitive data, because they are more likely to pay a big ransom.
Spyware
Spyware is a type of malware that monitors users’ activity and gathers information without their knowledge. A common type of a spyware is a keylogger, which captures all user keystrokes. This can lead to capturing login information and passwords.
Backdoor
A backdoor is a method of bypassing normal authentication or security measures to gain unauthorized access to a system. Backdoors are often installed by Trojans and allow attackers to control the system remotely, steal data, or install additional malware.
DDoS attack
DDoS is an abbreviation for Distributed Denial of Service. A DDoS attack involves overloading a server, network or website by sending large amounts of requests from multiple sources causing it to crash. A request is one device trying to communicate to another device telling it what to do (loading a website or accessing a file).
DDoS attacks are often performed by a botnet, a network of infected computers, usually by worms. Each computer in a botnet sends a request to the target, creating massive amounts of traffic eventually overwhelming and crashing the target.
(Crowdstrike, 2023)
Early stages and the first computer virus
Birth of the cyber world
Creation of the cyber world started in the mid-20th century with the development of the first computers. Their initial purpose was to transition from mechanical calculators to fully electronic systems. The first programmable computers took entire rooms, while having very limited use cases and small computational power.
The first multi-use computers, also called mainframe computers, were introduced in the 1960s. Notable ones include the IBM System/360. These computers were able to perform tasks like data analysis or simulations. They were quickly adopted by academic institutions. However up until this point in time, computers were not able to communicate with each other. This led to the invention of interconnected networks.
Interconnected networks were able to connect computer with each other, making data transfer a possibility. One of the first ones was a military system, called ARPANET, which was launched in 1969 and is the predecessor to modern day internet.
(Featherly, 2024)
Early computers were mainly focused on functionality and innovation. By design, they didn’t have any robust security features.
At the same time of these inventions, an American mathematical John von Neumann published a paper called Theory of Self-Reproducing Automata, in which he introduced the concept of the first self-replicating program, aka the first virus.
(Neumann, 1966)
First computer virus
In 1971, some researchers using the ARPANET system started seeing a weird message pop up on their screens, it read: “I’m the creeper: catch me if you can!”. This was the first ever computer virus, later dubbed The Creeper. Creeper was able to transfer to other computer computers connected to the same network. After a successful transfer, it would make a copy of itself and delete the old version on the previous computer.
(Matthews, 2022)
Luckily for the ARPANET users, displaying the message was all this virus did. It was only an experiment by other researchers to test the security features of networks and self-replication of a program. In response to the Creeper, another program called Reaper was developed. This was basically the first antivirus, designed to find copies of Creeper and delete them.
Even though the Creeper had hardly any consequences at the time, since the ARPANET was an isolated network with only a few individuals having access to it, it set the foundation for the future of computer viruses and cybersecurity.
(Isaacson, 2015)
Invention of personal computers
A breakthrough happened in 1971, with the introduction of the first ever personal computer, the Kenbak 1. This important step in computer history meant scaling down large mainframe computers, which were previously accessible only to specialized institutions, to a more compact form, similar to the ones we know today. However, Kenbak 1 didn’t achieve global adoption, as it was limited its functionality and production scale.
One of the first widely used personal computer was the IBM Personal Computer, which was made available for sale in 1981. Users were able to use analysis and simulation programs, text editors and even play games. Invention of this computer launched the software industry into one of the most important sectors in the economy.
(IBM, 2024)
Widespread adoption of the personal computers also sparked the need for data transportation, as the internet was not a thing yet. The world quickly adopted the use of floppy disk, which were invented about 10 years before. Floppy disks were able to store and transfer data between computers, with the first ones having capacity of about 360 KB, which could store about 1/5 of a photo taken on a modern phone. While being a great tool for transferring data, floppy disks introduced new vulnerabilities for computer viruses.
The first public virus
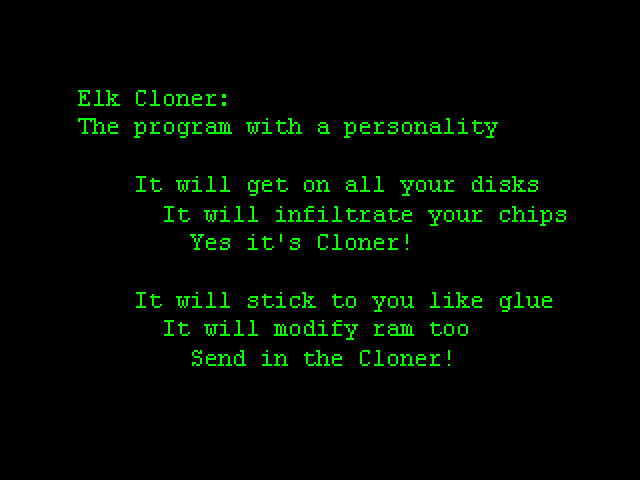
With a way of transporting data through floppy disks, viruses became more dangerous compared to the isolated systems like ARPANET. The first public virus was the Elk Cloner. It was created by a 15-year highschooler in 1982, Rich Skrenta and was designed to infect the Apple II computers.
The virus would attach itself to other legitimate programs on a floppy disk. Once it was inserted into a computer and booted, it would load into the computer memory. From there it would look for any uninfected floppy disk in the computer and make copies of itself into them. Overall, the virus wasn’t that harmful, as it didn’t delete or steal any data. But after every 50 boots, it would display a message. Since data had to be physically transferred through floppy disks, its spread was limited.
(Awati, 2024)
Figure 1 – Elk Cloner
Source: http://virus.wikidot.com/elk-cloner
The brain virus
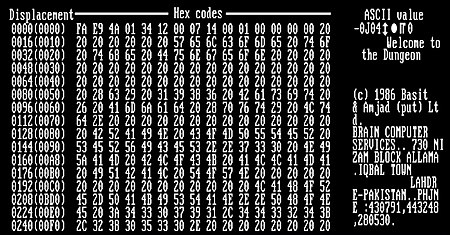
Another notable virus was developed in 1986, by the Farooq Alvi brothers Basit and Amjad who ran a computer store in Pakistan. They were selling a software, which people were copying without their permission. To combat this, they created the brain, a self-replicating virus that would infect the boot sector of the floppy disk and display a message to contact the creators. Even though their intent was to protect against piracy, the brain virus quickly got out of control and spread globally.
(IT, 2023)
Figure 2 – The Brain virus
Source: https://en.wikipedia.org/wiki/Brain_%28computer_virus%29
World wide web
Based on the network ARPANET, a British scientist Tim Berners-Lee working at CERN invented the world web in 1989 and launched to public on April 30th, 1993. This marked a significant milestone in cybersecurity history. Easy data transportation made way for faster spread of computer viruses.
(CERN, 2013)
The purpose of viruses shifted from mostly harmless pranks to a means of exploitation. New programs like ransomware locked important data and demanded a payment. Spywares and backdoors were used to steal confidential data from corporations and government. Self-replicating programs like viruses and worms targeted masses for plethora of different purposes.
Boom in the 2000s
The early 2000s sparked an internet revolution. The now global interconnected network of computers made a for perfect environment for the spread of viruses, due to the world wide web and the adoption of Microsoft operating systems, along with relatively undeveloped countermeasures and low public unawareness.
Compared to the viruses predating the internet, which were mostly harmless experiments, the 2000s is defined by massive virus outbreaks that caused billions USD in damages and infected millions of users.
ILOVEYOU
The ILOVEYOU virus is one of the most destructive viruses in history, infecting over 10 million Windows computers and causing near 15 billion USD in damages. It’s also one of the first viruses to use clever social engineering and public unawareness to spread.
Distribution
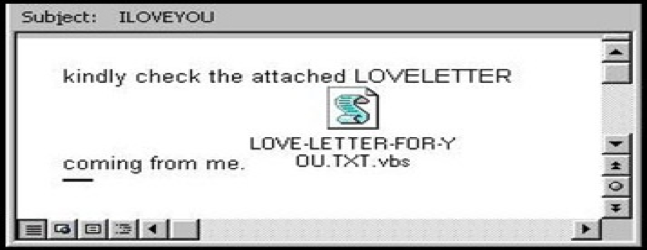
Imagine you are a working in an office in May 2000. You go to check your invoice and see this email.
Figure 3 – ILOVEYOU letter
Source: https://cyberhoot.com/cybrary/iloveyou-virus/
You decide to open the text file. For a split second, a program window opens and immediately closes. Thinking it’s an error, you move on and forget about this email. Later that day, you try to open an important work file but it’s corrupted. Looking for help, you go to send an email to one of your coworkers asking for help, only to discover hundreds of outgoing emails with the subject, text and file attachment.
How it worked
The most important thing about this virus isn’t the program itself, but the clever design of the distribution. The virus was written in Visual Basic for Applications (VBA), which is a programming language from Microsoft used for Office and interaction with the windows operating system.
With computers being a relatively new technology, most people didn’t realize that the extension of the file was “.VBS” and opened the file. This would execute the code written inside. Moreover, Windows had file extensions hidden by default, so the program would look like a normal .TXT file when copied onto the computer’s hard drive. Security measures were also underdeveloped at this time, not warning users about possible harm.
After being executed, ILOVEYOU would corrupt files in the computer. The virus would also exploit a vulnerability in Microsoft Outlook, sending the same email with the virus to all available contacts.
The program was created by a university student in the Philippines, Onel de Guzman. De Guzman originally created the virus to steal password for internet services, as he couldn’t afford to pay for them. However, he later adjusted the program to only cause harm. De Guzman admitted to creating the virus, but due to insufficient evidence and undeveloped laws against cybercrime, the charges against him were dropped.
(Root, 2022)
Impact
Within 24 hours of its release, ILOVEYOU infected millions of computers worldwide, from ordinary users to corporate and government subjects. It was the first virus of this magnitude and one of biggest in history. The caused damage includes corrupted data files, systems crashes, and overall panic. In total, it caused nearly 15 billion USD in damages.
As a direct result, Microsoft Outlook and other email providers began implementing security measures, such as fixing vulnerabilities and restricting the sharing of executable files via email. The public became more aware of computer viruses and corporations began cybersecurity trainings for employees. Countries also implemented stricter laws in regards to cybersecurity.
The success of the ILOVEYOU virus also inspired others to start creating similar programs, as it made people realize its destructive potential.
(Goldskysecurity, 2023)
Code Red
The Code Red is another worm that exploited a crucial vulnerability in Microsoft systems, specifically in Microsoft’s Internet Information Services (IIS), which is a web server software. It emerged in 2001, infecting hundreds of thousands of systems and causing significant damage.
How it worked
Code Red operated as a self-replicating worm that exploited a vulnerability in IIS servers. Once it infected a server, the worm scanned for other servers with the same vulnerability, exponentially spreading itself. It displayed a message on infected systems, which said: “HELLO! Welcome to http://www.worm.com! Hacked By Chinese!” Infected machines would also launch DDoS attacks, overwhelming website of its targets. Most famous was the attack on website of the White House. Because Code Red relied only on the connection to internet and didn’t require any user interaction, it spread rapidly.
(Berghel, 2001)
The exact creator of the Code Red worm remains unknown. The displayed message “Hacked by Chinese” suggest an origin for the virus, but that was never confirmed. Political motive due to the targeting of the white house was speculated, but no conclusion was ever reached.
Impact
Code Red infected over 359,000 servers within 14 hours of its discovery and caused estimated damages exceeding 2 billion USD, which mainly included the costs of system downtime from overloading networks by DDoS attacks.
The Code Red outbreak led to widespread adoption of firewalls and intrusion detection systems, as well as raising public awareness about dangers of computer viruses and the ways to protect against them.
MyDoom
The MyDoom first appeared in January 2004. It’s one of the fastest spreading and most destructive worms ever created, infecting millions of computers and causing billions USD in damages.
How it worked
MyDoom was very similar to the ILOVEYOU virus. It used clever social engineering to create and send vague emails with file attachments posing as legit files. The virus would arrive in an email titled “Error” or “Hello” with a message that would prompt users to open the attached file with a hidden executable code. Upon execution, the virus would embed itself into the system, harvest all email addresses and resend itself to all contacts.
Infected computers would become part of a botnet, which would launch DDoS attacks on chosen targets. With its rapid spread, these botnets became massive and could overload any website. MyDoom targeted websites of big companies like the SCO Group.
(Radware, 2024)
The true origin of MyDoom remains a mystery. The worm included the text “andy; I’m just doing my job, nothing personal, sorry”, leading to speculations about the motive for the creation of the virus. Sadly, the author was never found.
Impact
Overall, MyDoom caused over 30 billion USD in damages, stemming mainly from system downtime and repair costs. MyDoom exploited a lack of awareness about malicious email attachments. Organizations and individuals began implementing stricter email security protocols and educating users about phishing tactics.
(Okta, 2024)
Impact of the 2000s
The 2000s era was defined by outbreaks of rapidly spreading worms. Low public awareness and weak security measures allowed virus like ILOVEYOU to spread easily through emails. Most viruses were made with the motivation of mass disruption, corrupting data and causing system downtimes.
Threat of computer viruses sped up the development of more robust security measures, as well as public awareness. Companies trained their employees not to click on suspicious links or download vague executable files. Technologies like firewalls and antiviruses became more advanced and reliable in detecting malware.
Shift in the 2010s
With the technological advancement of malware countermeasures, malware itself had to be made more sophisticated in order to work. Motivation behind computer viruses went from causing mass disruption to monetizing cybercrime. The most common computer virus of this time was ransomware, a malware that upon infecting a system encrypts file and demands a payout for their decryption, usually through cryptocurrencies.
Cryptolocker
One of the most famous ransomwares, the Cryptolocker appeared in September 2013. This software would come in a form of email attachment that once executed would install itself onto the victim’s computer. The malware would encrypt user’s files and demand a ransom.
How it worked
Cryptolocker would come as an attachment in an email as a trojan, disguised as a legitimate file like PDF or a Word document. After user opened it, it would execute its code and infect the computer. Unlike worms in the past, Cryptolocker was not able to replicate and send itself to other users. This meant that its spread was far less rapid. The malware was mainly distributed by a botnet, a network of computers that would send emails containing the program.
Once inside the computer, Cryptolocker encrypted files using the RSA encryption. RSA is an asymmetric encryption method, meaning it has a private and a public key. This means that the decryption of the files is almost impossible without the private key.
Cryptolocker would then display a message, giving the user instructions on how to get the private key. This included paying a ransom, usually 300 USD, through sending bitcoin to a specific wallet.
(Kaspersky, 2024)
Figure 4 – Cryptolocker
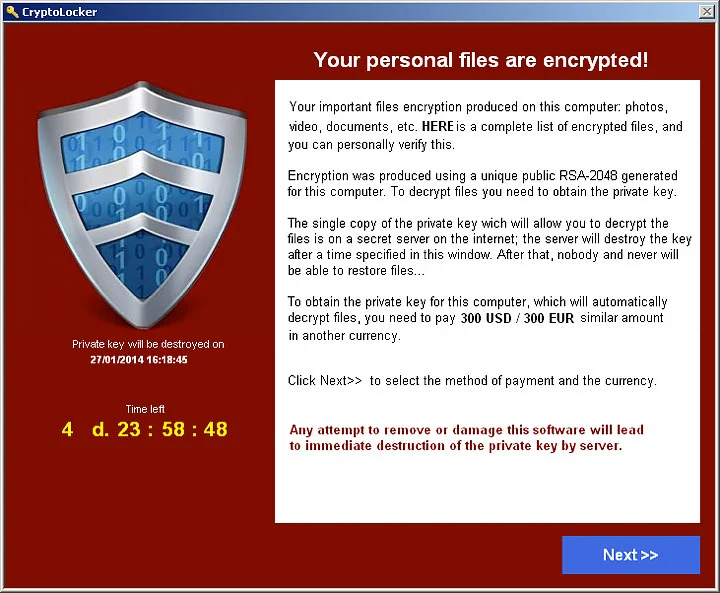
Source: https://www.knowbe4.com/cryptolocker-2
If the ransom wasn’t paid in time (usually 3-5 days) the private key would be destroyed and files forever lost.
Creator of this ransomware was never found, although some speculate that it was work of Evgeniy Mikhailovich Bogachev, a Russian cybercriminal. He’s connected to Cryptolocker through the botnet used for its distribution, but the link was never confirmed.
Impact
The estimated sum paid to the ranges from 3 to 30 million USD. However, a lot of victims did not pay the ransom, resulting in loss of files. This caused hundreds of millions USD in overall damages. Creation of Cryptolocker prompted companies and organizations to create more data backups to protect against possible future ransomware attacks.
WannaCry
In 2017 a new ransomware virus emerged, called WannaCry. This ransomware encrypted users’ data and demanded a ransom.
How it worked
WannaCry primarily targeted Windows computers. It exploited a vulnerability in the Windows Server Message Block (SMB) protocol, allowing it to spread without user interaction. The malware scanned for vulnerable systems and used the EteralBlue exploit to install itself, after which it encrypted user’s files and demanded a ransom.
Unlike Cryptolocker, WannaCry could spread like a worm, making it way more destructive as it infected more computers. Apart from that, it was really similar to Cryptolocker, using RSA to encrypt files and demanding a sum of money to be send to a crypto wallet before the private key was destroyed.
(Kaspersky, 2024)
Figure 5 – WannaCry
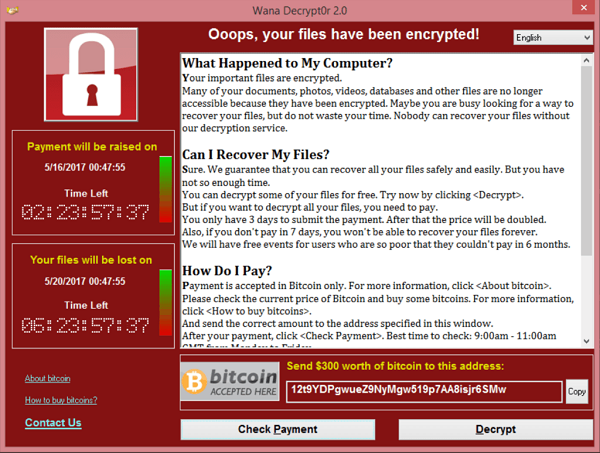
Source: https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
Impact
The WannaCry ransomware targeted over 230 000 computers and caused billions USD in damages. Its emergence prompted the use of data backups, as well as regularly updating operating systems, as this was the main reason why the malware worked.
Modern day
Modern day of malware is defined by constantly evolving threats as well as prevention techniques. The use of AI in antivirus as well as its technological advancement can prevent most attacks. Additionally, people have grown more aware of the dangers of viruses and companies training and prevention have gotten better. The use of malware has found its way into military use. Sophisticated programs are used for espionage, gather intelligence and disrupt critical infrastructure in times of war.
Smominru
Cryptocurrencies are one of the fastest growing financial instruments and their mining became popular at the end of the 2010s decade. The problem with crypto mining is that it requires a lot of computing power, resulting in expensive equipment and expensive electricity consumption. Smominru is an example of how new technologies result in the creation of new computer viruses.
How it works
Smominru is a cryptojacking malware, that infects computers and uses their CPU and GPU processing power to mine cryptocurrencies and send them to the attacker’s wallet. Smominru uses various techniques to access computers and use them to mine. This process runs in the background without any visual indications. It however drastically slows down the computer and consumes a lot of energy, resulting in high electricity bills for its victims.
(Harpaz, 2019)
Impact
Smominru first appeared in 2017 and is still active today. It can self-replicate and usually leaves a backdoor in the infected system, meaning even after detection and subsequent removal, the computer can be easily infected again.
(Hasman, 2022)
Other notable moder day viruses
Emotet, initially a banking Trojan, transformed into a botnet committing several cybercrimes before its end in 2021. Similarly, Ryuk has caused substantial financial damage by encrypting data and demanding ransom. The most common modern day malware include ransomware, spyware which use keylogger to detect user inputs and steal important data like banking information and trojans, which disguise themselves as legitimate programs.
(Fruhlinger, 2024)
Future
The emergence of new malware threats doesn’t look like it’s going to stop. To combat this, antivirus companies have started to incorporate AI and ML models to detect and deal with viruses. AI has the potential to detect abnormal activities and prevent virus infections proactively. On the other hand, same tools are available to attackers. AI malware could adapt its code dynamically making it more difficult to detect. However its development is expensive at time demanding, which in most cases makes it not worth the potential gain. Furthermore, with most viruses being developed by individuals or small groups with limited funding, it’s unlikely that AI malware is going to become the new norm.
(Khatabook, 2024)
Conclusion
Throughout the years, computer viruses have evolved from harmless pranks that explored the capabilities of systems, to sophisticated programs used for personal benefits such as demanding a ransom for encrypted data or mining cryptocurrencies. Their use even found its way into politics, propagating ideas and even into the military as tools for spying and causing mass disruption.