Introduction
The Transfer Control Protocol/Internet Protocol (TCP/IP) has emerged as a common means of communication worldwide. This is due to the ease of data sharing amongst networks. Its layered structure supports a variety of underlining applications of the internet from web surfing and using email services. With all its attributed significance in contemporary networking, it is critical to understand that TCP/IP was built with an emphasis on performance, not security. The situation is rapidly changing due to evolution of digital infrastructure where people require fast data transfer while privacy and compliance to regulations are respected. This position paper looks into structure, key protocols, services at the application-layer and security aspects of TCP/IP. It’s about new dangerous factors, legal systems the existence of which will make room for further development that can potentially enable securing of future internet communication.
This is a list of some important milestones in the TCP/IP evolution. It shows how TCP/IP grew from a fundamental project to the backbone of global communication. These milestones highlight its universal adoption and its role in establishing the modern Internet we rely on today.
1 Structure of TCP/IP
The suite of protocols called Transmission Control Protocol/Internet Protocol as referred to as TCP/IP has become the global standard and means for interconnecting hosts, networks and the internet which as such makes it one of the most influential inventions in facilitating the internet and networks around the globe. Though TCP/IP has a wide range of applications both the common ones and the rare ones, this entire set of applications rests on a set of basic protocols without which it is quite impossible to conceive the applications. Moreover, in order to comprehend what the workings of applications based on TCP/IP would be, one would need to understand what these basic protocols are.
1.1 History of TPC/IP
- 1969 – Four-node ARPANET established.
- 1973 – Development of TCP/IP suite begins.
- 1977 – An internet tested using TCP/IP.
- 1983 – TCP/IP becomes the official protocol for ARPANET.
- 1986 – NSFNET established.
- 1995 – Companies known as Internet Service Providers (ISPs) started.
This is a list of some important milestones in the TCP/IP evolution. It shows how TCP/IP grew from a fundamental project to the backbone of global communication. These milestones highlight its universal adoption and its role in establishing the modern Internet we rely on today.
1.2 TPC/IP protocol layers
TCP/IP is design in layers, creating the protocol stack. This stack allows for division of labour, ease of implementation, code testing, and the development of alternative layer implementations. Layers communicate via concise interfaces, providing services for the layer above and using services provided by the layer below. For example, the IP layer transfers data without guaranteeing reliable delivery or duplicate suppression, enabling applications to receive in-order data stream delivery.
1.2.1 Application Layer
The application layer is a program that uses TCP/IP for communication; it allows user processes to cooperate with another process on different hosts. Examples include Telnet and FTP. The interface is defined by port numbers and sockets.
1.2.2 Transport Layer
The transport layer provides a means for end-to-end data transfer between applications across multiple applications concurrently. Most commonly used protocol is the Transmission Control Protocol (TCP) because it offers reliable data delivery, duplicate suppression, congestion control, and flow control. The User Datagram Protocol (UDP) provides a connectionless, unreliable best-effort service, placing the responsibility of end-to-end integrity, flow control, and congestion control within the applications.
1.2.3 Internetwork Layer
The Internetwork layer, also called the network layer, offers the virtual network image of an internet to higher layers shielding them from physical network architecture. The most important protocol of this layer is the Internet Protocol; the protocols offer routing functions to transmit the messages to their destination. The protocols include IP, ICMP, IGMP, ARP, and RARP.
1.2.4 Network Interface Layer
The network interface layer connects to the network hardware below it and can be oriented to packets or streams. TCP/IP does not specify a link protocol but instead can operate any number of network interfaces – a reflection of the IP layer’s flexibility.
1.3 TPC/IP architecture
Application protocols are the highest layer interfaces in any internet host using the TCP/IP protocol stack. These protocols may be user-written or standardized and form part of the TCP/IP product. Examples include Telnet for terminal access, FTP for high-speed file transfers, and SMTP for internet mailing. Most applications use either UDP or TCP as a transport mechanism, with TCP being more reliable and allowing flow control. Some applications use UDP for improved performance. Most applications use the client/ server model of interaction. Each TCP/IP implementation includes a smaller or larger set of application protocols.
1.3.1 The client/server model
TCP is a peer-to-peer, connection-oriented protocol with no masters or subordinates. Applications usually communicate using a client-server model. A server is any application that provides services to users on the Internet. A client is one that requests a service. An application includes both a server and client part, which can either run on the same system or on different systems. Users invoke the client part, which forms a request for a service and sends it to the server part using TCP/IP. The server receives a request, performs the required service, and sends back results in a reply. Most servers wait at a well-known port for requests, but clients use an arbitrary ephemeral port to talk to it.
1.3.2 Bridges, routers, and gateways
A router is an internetworking device that connects networks at the network interface layer level allowing remote access to networks. It functions as a MAC relay and is transparent to IP. A router connects networks at the internetwork layer level and routes packets between them. It must understand the addressing structure associated with the networking protocols it supports and make decisions on whether or how to forward packets. The basic routing function is implemented in the IP layer of the TCP/ IP protocol stack. A router is visible to IP and can forward IP datagrams to the target host. A gateway connects networks at higher layers, usually supporting address mapping and end-to-end application connectivity. It is also opaque to IP and only sends IP datagrams to a gateway. Firewalls or firewall gateways are used to restrict access from the Internet or an untrusted network to an organization-controlled network due to security reasons.
2 TCP/IP Application Layer Protocols
The application layer in the TCP/IP Model represents a combination of the OSI model’s application, presentation, and session layers. It is responsible for initiating software programs to transfer data across the network. Presentation takes care of formatting the data so that it is understandable to the recipient. The different application layer protocols like HTTP, HTTPS, FTP, SMTP, POP3, IMAP, DNS, SNMP, Telnet, and DHCP enable the exchange of information between users. HTTPS is commonly used to secure data in transit. Each of these protocols has performance, security, and privacy issues.
2.1 HTTP & HTTPS
HTTP is the protocol of the application layer of a client-server architecture that allows communications between web browsers and servers. The security for data being transferred over the internet is very powerful with HTTP; it has integrity and confidentiality. However, several researchers view that HTTPS implementation causes higher power consumption and lack of flexibility that hampers performance and functionality.
While giant sites such as Facebook and YouTube have already widely adopted HTTPS as the standard protocol of secure communication, HTTPS has strong security benefits, its implications on power consumption and flexibility should be considered in designing Internet applications.
HTTPS reduces security vulnerability by including either SSL certificates or TLS, allowing for the security of encrypted connections between the server and the browser. This encryption serves to prevent any possible interception of personal data, including credit card numbers and passwords. Authentication plays another significant role in HTTPS by ensuring that both the server and the client can validate each other’s identities.
2.2 Telnet
Telnet is a TCP/IP protocol that connects to remote devices and makes local terminals appear directly connected to remote systems. It is a communication tool between users and remote devices. Telnet is used by network administrators in accessing remote devices for administration.
2.3 Secure Shell (SSH)
Secure Shell (SSH) is a secure alternative to Telnet, enabling users to manage and manipulate remote servers securely. It utilizes cryptography to ensure that communication is encrypted and secure. SSH authenticates the remote user and uses various encryption methods, such as Symmetric Encryption, which uses the same secret key for encryption and decryption, and Asymmetric Encryption, which uses different public and private keys for encryption and decryption, respectively, including but not limited to ciphers like RSA and Diffie-Hellman.
2.4 SMTP
The Simple Mail Transfer Protocol is an MTA that runs on port 25 and outlines the client and server MTAs in the exchange of email. It basically sets standards for data exchange between the two by command and response and thus provides a smooth structure for the transfer of emails over the Internet.
2.5 Post Office Protocol version 3 (POP3)
In the third phase of email retrieval, messages are pulled from the mail server to the recipient using a pull program. Here, message access agents are used, for example, Post Office Protocol version 3, abbreviated as POP3, which uses port number 110. The users connect to the server using a username and password for secure message retrieval.
2.6 IMAP 4
IMAP4 – Internet Mail Access Protocol version 4, is on Port 993 and has advanced capabilities than POP3 with more complex capabilities. These include previewing an e-mail without downloading it, download a partial of an e-mail, and actions such as creating, deleting, or renaming mailboxes on the mail server that hosts your account. The described capabilities also make IMAP4 more flexible than POP3.
2.7 File Transfer Protocol (FTP)
File Transfer Protocol-FTP is a protocol that uses TCP services to replicate the files between hosts. It establishes two connections: one for data transfer and the other for control information. The Control Connection remains open during the life of the FTP session, while the data transfer process uses the open connection for file transfer. The FTP model is shown below.
3 Security Concerns in Web Applications and Browsers
3.1 Caching Issues
Every Web browser caches pages visited by users in a temporary cache; this cache can be accessed by an attacker without authenticating any details like images, passwords, and usernames. These factors therefore raise several privacy issues. These risks can be reduced by regular clearance and disabling auto-saving of data.
3.2 Session Hijacking
Session hijacking is an attack wherein a hacker ‘acquires’ an HTTP session by intercepting and stealing packets through packet sniffers. Successful session hijacking provides the hacker with full access and redirects communication from the client to the attacker. Such possible attacks require additional security measures in relation to authentication.
3.3 Cookie Poisoning
Cookies keep the session information, avoiding time-wasting frequent logins. However, the modification or theft of cookies could present possible attacks on personal information. When the attacker obtains a cookie holding login credentials, it may be used without verification; therefore, this is dangerous and presents an unauthorized access/ identity theft threat. These are prevented by the Web Application Firewalls.
3.4 Replay Attack
A replay attack is a cyber-attack where an unauthorized user intercepts and retransmits data, potentially altering it and redirecting the user’s machine to an unintended destination. To mitigate replay attacks, web browsers should implement session tracking mechanisms that distinguish legitimate from replayed traffic.
3.5 Cross-Site Scripting
Cross-Site Scripting (XSS) is an attack where malicious attackers inject malicious code into a web application or browser to hijack the user’s session by stealing session tokens and cookies. In defence, websites can disable the scripts, but this would minimize features. Another strategy would be to enhance security controls around cookie-based user authentication.
3.6 Domain Name System
The DNS is an essential component of the internet that translates human-readable domain names into IP addresses. Attackers manipulate DNS records, which cause incorrect IP addresses and redirecting of legitimate traffic to malicious servers using protocol attacks.
3.7 DNS Protocol Attacks
DNS protocol attacks take advantage of vulnerabilities in network functions such as DNS cache poisoning, DNS spoofing, and DNS ID hijacking. These different kinds of attacks manipulate DNS cache, give wrong mappings, and redirect requests to malicious sites. DNS spoofing forges IP addresses to misdirect requests, while DNS ID hijacking impersonates a DNS server. Keeping the DNS server operating systems updated and implementing DNS Security Extensions will help prevent these attacks.
3.8 Dynamic Host Configuration Protocol (DHCP)
The Dynamic Host Configuration Protocol is used to assign temporary IP addresses to client machines on an IP network. Attackers take advantage of this and implement a DHCP starvation attack against any host, thereby sending false requests to the server until the server becomes overloaded.
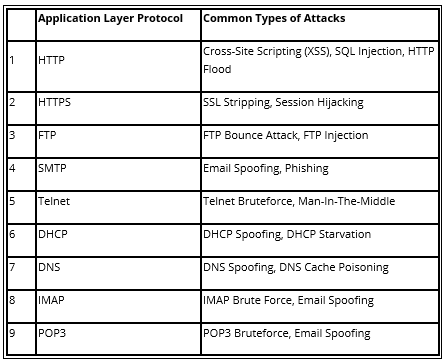
3.9 Summary of the common attacks
It can prevent denial-of-service, whereby port security on the switch limits MAC addresses per port. This enables the DHCP server to effectively manage the allocation of IP addresses. The common application layer protocols attacks are summarized in Table 1.
4 Security and Privacy
The TCP/IP Application Layer faces significant security and privacy challenges, including Man-in-the-Middle (MitM) attacks, session hijacking, and unauthorized access. These vulnerabilities affect user-centric protocols such as HTTP, Telnet, and FTP, making system protection a critical concern. Proper system management and adherence to organizational or governmental security standards can reduce these risks.
Administrators may be required to comply with certain levels of security related to corporate policies or compliance laws like the U.S. DOD standards and the General Data Protection Regulation by the European Union. The standards encompass all aspects of the network infrastructure ranging from the operating system and application software to the administrative tools AIX System Management Guide, TCP/IP Security.
While TCP/IP security features ensure system protection, the balance between security and privacy and compliance remains tricky:
- Data Confidentiality vs. Monitoring: Administrators may monitor network traffic for security reasons, but such monitoring should be compliant with privacy regulations like GDPR, requiring transparency and minimal data retention.
- Encryption vs. System Performance: Enabling encryption through SSL/TLS enhances privacy but increases processing loads and network latency.
- Access Control vs. Usability: The implementation of strict access controls, such as multi-factor authentication, strengthens security but may inconvenience users and reduce productivity.
It is here that organizations have to balance these trade-offs by integrating technical and administrative policies, ensuring security mechanisms comply with industry standards while respecting user privacy.
Conclusions
TCP/IP protocols are complicated but have really revolutionized internet communication by establishing a universal standard for the transfer of data across networks. Their flexibility in design has enabled the creation of an innumerable number of applications and services that power the modern digital world. This success comes at a price, though: significant security and privacy issues. Such threats as general weaknesses, such as session hijacking and DNS spoofing, encryption, regulatory, as well as many others, make security measures most needed while transmitting information over the Internet. As organizations operate against the backdrop of numerous privacy regulations and constantly evolving cyber threats, strengthening the TCP/IP protocols through cryptography, authenticated access, and trusted computing remains key. Otherwise, a balance of security, privacy, and performance would have to be struck so that the next phase of internet usage on a global scale would evolve as planned without sacrificing the users’ confidence in it.
List of references
Forouzan, B. A. (2010). TCP/IP protocol suite (4. ed). McGraw-Hill Higher Education.
Leiden, C. (with Wilensky, M.). (2009). TCP/IP for dummies (6th ed). Wiley.
(PDF) Performance, Privacy, and Security issues of TCP/IP at the Application Layer: A Comprehensive Survey. (2024). ResearchGate. https://doi.org/10.30574/gscarr.2024.18.3.0106
Parziale, L. & International Business Machines Corporation (Eds.). (2006). TCP/IP tutorial and technical overview (8th ed). IBM International Technical Support Organization.